Ransomware is a type of malware that prevents or limits users from accessing their system and data. This type of malware forces its victims to pay the ransom through online payment methods to restore access to their systems, or to get their data back. Ransomware can be downloaded by unknowing users who visit malicious or compromised websites. Some ransomware is delivered as attachments to spammed email often from usernames we recognize.
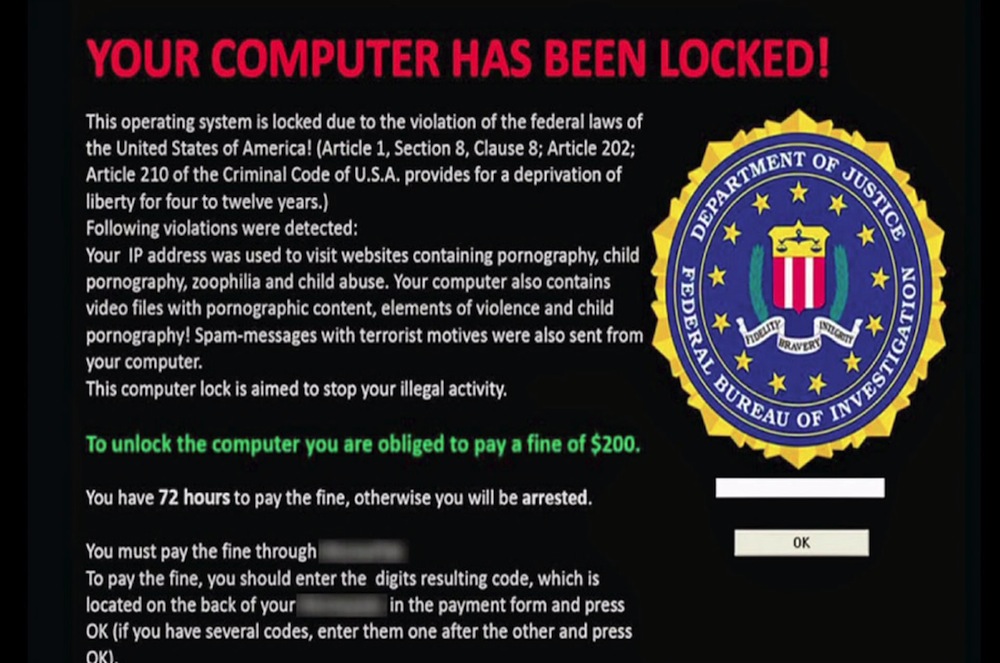
Once executed in the system, some ransomware can either lock the computer screen or encrypt pre-determined files or all data files with a complex encryption algorithm. In the first scenario, a ransomware shows a screen image or notification, which prevents victims from using their system. This screen also provides instructions on how users can pay the ransom.
The second type of ransomware encrypts files including word processing documents, spreadsheets, photos and other important files making it impossible for the user to work. The terrorist behind ransomware make use of online payment methods such as Bitcoins as a way for users to pay the ransom. However, paying the ransom doesn’t guarantee the cybercriminal will restore your system or files to you.
Who Are Ransomware’s Prime Targets?
Any company or organization that depends on daily access to critical data—and can’t afford to lose access to it during the time it would take to respond to an attack—should be most worried about ransomware.
To help avoid being infected by Ransomware follow these guidelines.
Always check who the email sender is If the email came from a personal contact, confirm if your friend sent the message.
Check the content of the message There are obvious factual errors or discrepancies that you can read. Example, if your bank or a friend claims that they have received something from you, try to go to your recently sent items to double-check their claim. Such spammed messages can also use other social engineering lures to persuade users to open the message.
Refrain from clicking links in emails In general, clicking on links in email should be avoided. If you want to visit the site it is better to type in the name yourself.
Always ensure your software is up-to-date Update your operating system regularly. Most update automatically but be sure to allow the updates to finish. If you are still using an older operating system consider an upgrade to the latest version. Make sure your Antivirus is updates and active.
Backup important data The best defense against ransomware is to outwit attackers by not being vulnerable to their threats in the first place. This means backing up important data daily. There are little to no tools for decrypting a ransomware file. The best computing practice is to ensure you have accurate backups of your files. You should have three copies, on different medias with one at an offsite location. Some ransomware attackers search out backup systems to encrypt and lock by first gaining entry to desktop systems and then manually working their way through a network to get to servers. So if you don’t back up to the cloud and instead backup to a local storage device or server, these should be offline and not directly connected to desktop systems where the ransomware or attacker can reach them.
Got An Infection! Shut down Immediately disconnect systems from the network to stop the spread and encryption of files. After that, victim should determine the strain of ransomware infected them. If it’s a known variant and the best way to recover from a backup. if you haven’t backed up your data and can’t find a method to get around the encryption, your only option to get access to your data is to pay the ransom. Although the FBI recommends not paying,
Block that BUG! Users should never be considered the blocker for any type of malware. Users will open attachments, they will visit sites that are infected, and when that happens, you just need to make sure that your security technology protects you. Make sure you have an antivirus that reports back to you. Many of the newer cloud based setups update admins immediately when a virus attacks a system giving administrators the best change to stop the damage.